How to Secure Your SaaS Application in 2025
In 2025, Software-as-a-Service (SaaS) continues to dominate the digital economy, offering unmatched flexibility, scalability, and cost-effectiveness. But with innovation comes new and complex security challenges.
Cyber threats are evolving rapidly. Data breaches, ransomware, credential theft, and insider threats are no longer isolated incidents—they’re daily concerns. For SaaS providers, failing to implement robust security practices can lead to more than just downtime or financial loss—it can result in regulatory penalties, customer churn, and long-term brand damage.
So, how do you effectively secure your SaaS application in today’s high-risk environment? Here’s a practical, up-to-date guide.
The 2025 Security Landscape: What’s Changed?
Modern security isn’t about just firewalls and passwords anymore. Several key trends are reshaping the way we defend SaaS platforms:
- AI-Powered Attacks: Cybercriminals now harness AI to automate phishing, malware deployment, and credential stuffing attacks at scale.
- Expanded Attack Surface: With remote and hybrid work here to stay, users are accessing systems from various devices and locations—introducing new endpoint risks.
- Zero-Day Exploits: Vulnerabilities are being discovered and sold on the dark web before vendors even know they exist.
- Third-Party Dependencies: Today’s SaaS apps often rely on numerous integrations, APIs, and microservices—each one a potential threat vector.
To stay ahead, you need a layered, proactive, and intelligent approach to security.
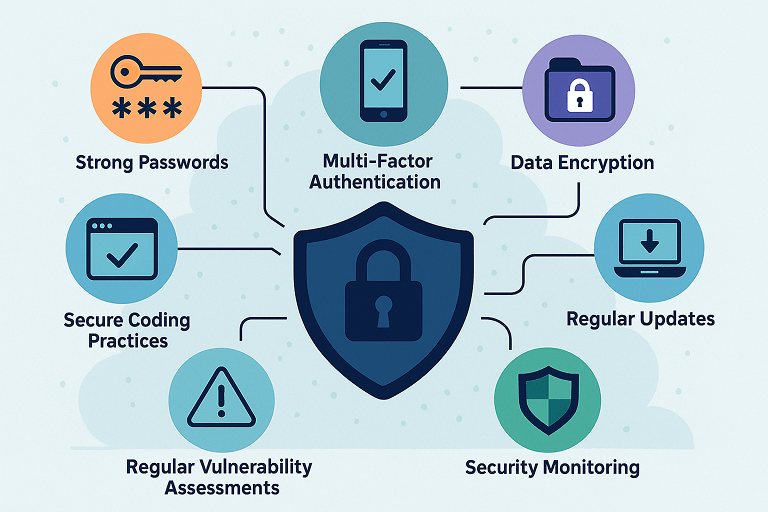
1. Embrace a Zero Trust Architecture
Zero Trust means assuming nothing and verifying everything. No user or device should be trusted automatically, whether inside or outside the corporate network.
How to implement:
- Enforce Multi-Factor Authentication (MFA) across all accounts.
- Apply least privilege access, granting users only what they absolutely need.
- Continuously monitor all access attempts and maintain comprehensive audit logs.
By treating every access request as a potential threat, you greatly reduce the chances of internal and external breaches.
2. Encrypt Everything—At Rest and In Transit
Encryption is still a cornerstone of modern security, especially as data moves across cloud environments.
- Use TLS 1.3 to encrypt all data in transit.
- Apply AES-256 encryption to all stored data, including backups.
- Implement a secure and isolated Key Management System (KMS) with strict access controls.
Encryption helps ensure that even if data is intercepted or accessed, it remains unintelligible to bad actors.
3. Secure Your APIs and Third-Party Integrations
APIs are integral to SaaS functionality but are frequently exploited by attackers.
Best practices:
- Require API authentication, implement rate limiting, and apply throttling to prevent abuse.
- Always validate and sanitize input data to avoid injection attacks.
- Conduct regular vendor audits and revoke access to unused or dormant integrations.
Third-party connections must be treated with the same scrutiny as internal components.
4. Invest in Continuous Monitoring and Threat Detection
Security threats don’t follow a 9-to-5 schedule. You need real-time visibility and intelligent detection to catch issues before they escalate.
- Deploy AI-driven SIEM (Security Information and Event Management) tools for real-time threat detection.
- Use behavioral analytics to identify anomalies in user behavior or system activity.
- Partner with a Security Operations Center (SOC) or an MDR (Managed Detection and Response) provider for 24/7 protection.
Proactive monitoring enables faster response times and minimizes damage during an attack.
5. Conduct Regular Penetration Testing and Vulnerability Scans
Even the most robust applications can harbor unseen vulnerabilities.
- Schedule quarterly penetration tests conducted by certified ethical hackers.
- Perform automated vulnerability scans after every major release.
- Launch a bug bounty program to invite external security researchers to report potential flaws.
By simulating real-world attacks, you’ll uncover weaknesses before hackers do.
6. Compliance Is Not Optional—It's a Baseline
Regulatory frameworks aren’t just legal checkboxes—they’re a foundation for customer trust and operational integrity.
Ensure compliance with:
- Standards like GDPR, HIPAA, SOC 2, ISO 27001, and industry-specific regulations.
- Data sovereignty laws relevant to your operating regions.
- Transparent privacy policies and explicit user consent mechanisms.
Being compliance-ready protects your business and reassures your users.
7. Educate Your Team and Your Users
Technology can only go so far. People remain the weakest—and strongest—link in your security chain.
- Train your employees on phishing awareness, social engineering tactics, and secure coding practices.
- Educate end-users on creating strong passwords, recognizing suspicious activity, and how to report concerns.
- Conduct periodic security drills to keep everyone alert and prepared.
Security is a shared responsibility—and it starts with awareness.
How Techrover™ Can Help You Stay Secure
At Techrover Solutions, we specialize in building secure, future-proof SaaS platforms tailored to the realities of 2025. Here’s how we support your security journey:
✅ Secure-by-Design SaaS Development – We embed security principles at every development layer.
✅ Compliance-Ready Architecture – Our solutions align with industry standards from day one.
✅ Ongoing Security Monitoring – We offer real-time threat detection and response through managed services.
✅ Rapid Incident Response – In the event of a breach, we help you contain, recover, and improve.
✅ Security Consulting & Training – Equip your team with expert-led security training and strategy.
Ready to Future-Proof Your SaaS Security?
Cybersecurity isn’t a one-time investment—it’s an ongoing commitment. Whether you’re building a new product or improving an existing platform, now is the time to strengthen your defenses.
Let Techrover™ Solutions be your trusted partner in building secure, scalable, and resilient SaaS applications—today and tomorrow.
Let’s build trust—through security.


